Hash functions
A hash function takes a string and produces a fixed-length string based on the input. The output string is called the hash value. Ideal hash functions obey the following:
- It should be very difficult to guess the input string based on the output string.
- It should be very difficult to find 2 different input strings having the same hash output.
- It should be very difficult to modify the input string without modifying the output hash value.
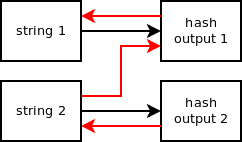
Hash functions can be used to calculate the checksum of some data. It can be used in digital signatures and authentication. We will see some applications in details later on.
Let’s look at one example of a hash function: SHA-256
SHA-256
Hashing a value using SHA-256 is done this way:
1 | >>> from Crypto.Hash import SHA256 |
2 | >>> SHA256.new('abc').hexdigest() |
3 | 'ba7816bf8f01cfea414140de5dae2223b00361a396177a9cb410ff61f20015ad' |
It is important to know that a hash function like MD5 is vulnerable to collision attacks. A collision attack is when two different inputs result in the same hash output. It is also vulnerable to some preimage attacks found in 2004 and 2008. A preimage attack is: given a hash h, you can find a message m where hash(m) = h.
Applications
Hash functions can be used in password management and storage. Web sites usually store the hash of a password and not the password itself so only the user knows the real password. When the user logs in, the hash of the password input is generated and compared to the hash value stored in the database. If it matches, the user is granted access. The code looks like this:
1 | from Crypto.Hash import SHA256 |
2 | def check_password(clear_password, password_hash): |
3 | return SHA256.new(clear_password).hexdigest() == password_hash |
It is recommended to use a module like py-bcrypt to hash passwords as it is more secure than using a hash function alone.
Another application is file integrity checking. Many downloadable files include a MD5 checksum to verify the integrity of the file once downloaded. Here is the code to calculate the MD5 checksum of a file. We work on chunks to avoid using too much memory when the file is large.
02 | from Crypto.Hash import MD5 |
03 | def get_file_checksum(filename): |
06 | with open(filename, 'rb') as f: |
08 | chunk = f.read(chunk_size) |
Hash functions comparison
| Hash function | Hash output size (bits) | Secure? |
|---|
| MD2 | 128 | No |
| MD4 | 128 | No |
| MD5 | 128 | No |
| SHA-1 | 160 | No |
| SHA-256 | 256 | Yes |
Encryption algorithms
Encryption algorithms take some text as input and produce ciphertext using a variable key. You have 2 types of ciphers: block and stream. Block ciphers work on blocks of a fixed size (8 or 16 bytes). Stream ciphers work byte-by-byte. Knowing the key, you can decrypt the ciphertext.
Block ciphers
Let’s look at one of the block cipher: DES. The key size used by this cipher is 8 bytes and the block of data it works with is 8 bytes long. The simplest mode for this block cipher is the electronic code book mode where each block is encrypted independently to form the encrypted text.

It is easy to encrypt text using DES/ECB with pycrypto. The key ‘10234567’ is 8 bytes and the text’s length needs to be a multiple of 8 bytes. We picked ‘abcdefgh’ in this example.
1 | >>> from Crypto.Cipher import DES |
2 | >>> des = DES.new('01234567', DES.MODE_ECB) |
4 | >>> cipher_text = des.encrypt(text) |
6 | '\xec\xc2\x9e\xd9] a\xd0' |
7 | >>> des.decrypt(cipher_text) |
A stronger mode is CFB (Cipher feedback) which combines the plain block with the previous cipher block before encrypting it.
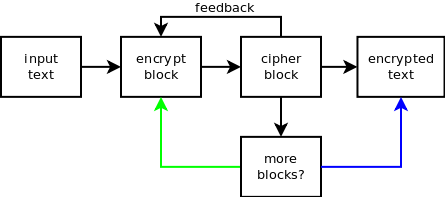
Here is how to use DES CFB mode. The plain text is 16 bytes long (multiple of 8 bytes). We need to specify an initial feedback value: we use a random string 8 bytes long, same size as the block size. It is better to use a random string for each new encryption to avoid chosen-ciphertext attacks. Note how we use two DES objects, one to encrypt and one to decrypt. This is required because of the feedback value getting modified each time a block is encrypted.
01 | >>> from Crypto.Cipher import DES |
02 | >>> from Crypto import Random |
03 | >>> iv = Random.get_random_bytes(8) |
04 | >>> des1 = DES.new('01234567', DES.MODE_CFB, iv) |
05 | >>> des2 = DES.new('01234567', DES.MODE_CFB, iv) |
06 | >>> text = 'abcdefghijklmnop' |
07 | >>> cipher_text = des1.encrypt(text) |
09 | "?\\\x8e\x86\xeb\xab\x8b\x97'\xa1W\xde\x89!\xc3d" |
10 | >>> des2.decrypt(cipher_text) |
Stream ciphers
Those algorithms work on a byte-by-byte basis. The block size is always one byte. Two algorithms are supported by pycrypto: ARC4 and XOR. Only one mode is available: ECB.
Let’s look at an example with the algorithm ARC4 using the key ‘01234567’.
1 | >>> from Crypto.Cipher import ARC4 |
2 | >>> obj1 = ARC4.new('01234567') |
3 | >>> obj2 = ARC4.new('01234567') |
4 | >>> text = 'abcdefghijklmnop' |
5 | >>> cipher_text = obj1.encrypt(text) |
7 | '\xf0\xb7\x90{#ABXY9\xd06\x9f\xc0\x8c ' |
8 | >>> obj2.decrypt(cipher_text) |
Applications
It is easy to write code to encrypt and decrypt a file using pycrypto ciphers. Let’s do it using DES3 (Triple DES). We encrypt and decrypt data by chunks to avoid using too much memory when the file is large. In case the chunk is less than 16 bytes long, we pad it before encrypting it.
02 | from Crypto.Cipher import DES3 |
04 | def encrypt_file(in_filename, out_filename, chunk_size, key, iv): |
05 | des3 = DES3.new(key, DES3.MODE_CFB, iv) |
07 | with open(in_filename, 'r') as in_file: |
08 | with open(out_filename, 'w') as out_file: |
10 | chunk = in_file.read(chunk_size) |
13 | elif len(chunk) % 16 != 0: |
14 | chunk += ' ' * (16 - len(chunk) % 16) |
15 | out_file.write(des3.encrypt(chunk)) |
17 | def decrypt_file(in_filename, out_filename, chunk_size, key, iv): |
18 | des3 = DES3.new(key, DES3.MODE_CFB, iv) |
20 | with open(in_filename, 'r') as in_file: |
21 | with open(out_filename, 'w') as out_file: |
23 | chunk = in_file.read(chunk_size) |
26 | out_file.write(des3.decrypt(chunk)) |
Next is a usage example of the two functions defined above:
01 | from Crypto import Random |
02 | iv = Random.get_random_bytes(8) |
03 | with open('to_enc.txt', 'r') as f: |
04 | print 'to_enc.txt: %s' % f.read() |
05 | encrypt_file('to_enc.txt', 'to_enc.enc', 8192, key, iv) |
06 | with open('to_enc.enc', 'r') as f: |
07 | print 'to_enc.enc: %s' % f.read() |
08 | decrypt_file('to_enc.enc', 'to_enc.dec', 8192, key, iv) |
09 | with open('to_enc.dec', 'r') as f: |
10 | print 'to_enc.dec: %s' % f.read() |
The output of this script:
1 | to_enc.txt: this content needs to be encrypted. |
3 | to_enc.enc: ??~?E??.??]!=)??"t? |
4 | JpDw???R?UN0?=??R?UN0?}0r?FV9 |
5 | to_enc.dec: this content needs to be encrypted. |
Public-key algorithms
One disadvantage with the encryption algorithms seen above is that both sides need to know the key. With public-key algorithms, there are two different keys: one to encrypt and one to decrypt. You only need to share the encryption key and only you can decrypt the message with your private decryption key.
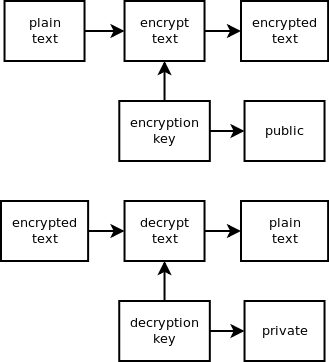
Public/private key pair
It is easy to generate a private/public key pair with pycrypto. We need to specify the size of the key in bits: we picked 1024 bits. Larger is more secure. We also need to specify a random number generator function, we use the Random module of pycrypto for that.
1 | >>> from Crypto.PublicKey import RSA |
2 | >>> from Crypto import Random |
3 | >>> random_generator = Random.new().read |
4 | >>> key = RSA.generate(1024, random_generator) |
6 | <_RSAobj @0x7f60cf1b57e8 n(1024),e,d,p,q,u,private> |
Let’s take a look at some methods supported by this key object. can_encrypt() checks the capability of encrypting data using this algorithm. can_sign() checks the capability of signing messages. has_private() returns True if the private key is present in the object.
Encrypt
Now that we have our key pair, we can encrypt some data. First, we extract the public key from the key pair and use it to encrypt some data. 32 is a random parameter used by the RSA algorithm to encrypt the data. This step simulates us publishing the encryption key and someone using it to encrypt some data before sending it to us.
1 | >>> public_key = key.publickey() |
2 | >>> enc_data = public_key.encrypt('abcdefgh', 32) |
4 | ('\x11\x86\x8b\xfa\x82\xdf\xe3sN ~@\xdbP\x85 |
5 | \x93\xe6\xb9\xe9\x95I\xa7\xadQ\x08\xe5\xc8$9\x81K\xa0\xb5\xee\x1e\xb5r |
6 | \x9bH)\xd8\xeb\x03\xf3\x86\xb5\x03\xfd\x97\xe6%\x9e\xf7\x11=\xa1Y<\xdc |
7 | \x94\xf0\x7f7@\x9c\x02suc\xcc\xc2j\x0c\xce\x92\x8d\xdc\x00uL\xd6. |
8 | \x84~/\xed\xd7\xc5\xbe\xd2\x98\xec\xe4\xda\xd1L\rM`\x88\x13V\xe1M\n X |
9 | \xce\x13 \xaf\x10|\x80\x0e\x14\xbc\x14\x1ec\xf6Rs\xbb\x93\x06\xbe',) |
Decrypt
We use the private key to decrypt the data.
1 | >>> key.decrypt(enc_data) |
Sign
Signing a message can be useful to check the author of a message and make sure we can trust its origin. Next is an example on how to sign a message. The hash for this message is calculated first and then passed to the sign() method of the RSA key. You can use other algorithms like DSA or ElGamal.
1 | >>> from Crypto.Hash import SHA256 |
2 | >>> from Crypto.PublicKey import RSA |
3 | >>> from Crypto import Random |
4 | >>> key = RSA.generate(1024, random_generator) |
6 | >>> hash = SHA256.new(text).digest() |
8 | '\x9cV\xccQ\xb3t\xc3\xba\x18\x92\x10\xd5\xb6\xd4\xbfWy\r5\x1c\x96\xc4|\x02\x19\x0e\xcf\x1eC\x065\xab' |
9 | >>> signature = key.sign(hash, '') |
Verify
Knowing the public key, it is easy to verify a message. The plain text is sent to the user along with the signature. The receiving side calculates the hash value and then uses the public key verify() method to validate its origin.
2 | >>> hash = SHA256.new(text).digest() |
3 | >>> public_key.verify(hash, signature) |
That’s it for now. I hope you enjoyed the article. Please write a comment if you have any feedback.



